What is Security?
When we say 'Security,' we are referring to one of three things:
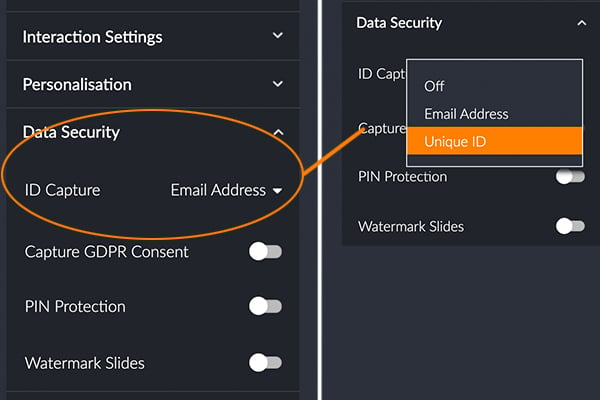
1. Security of Access
|
2. Security of Content
In addition to the security controls determining who gets into an event or session, you should also look to add a layer of security to your content and intellectual property.
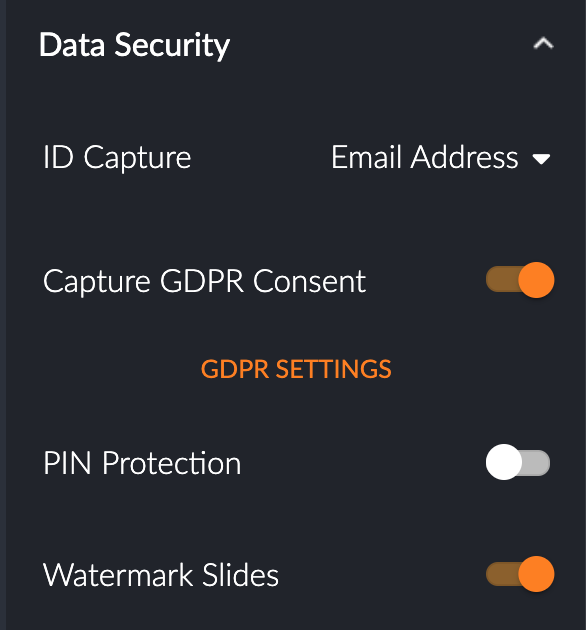
In a physical event we've mostly accepted that people have cameras in their phones and have the ability to capture presentation content. With virtual, we have to go the extra step and discourage screen-grabbing. Our watermark feature delivers this, overlaying delegate details on the on screen and downloaded slide images, allowing better tracing of any leaked content.
 |
|
Toggle on 'Watermark Slides' to better secure your presentation content. |
3. Security of Delegate Data
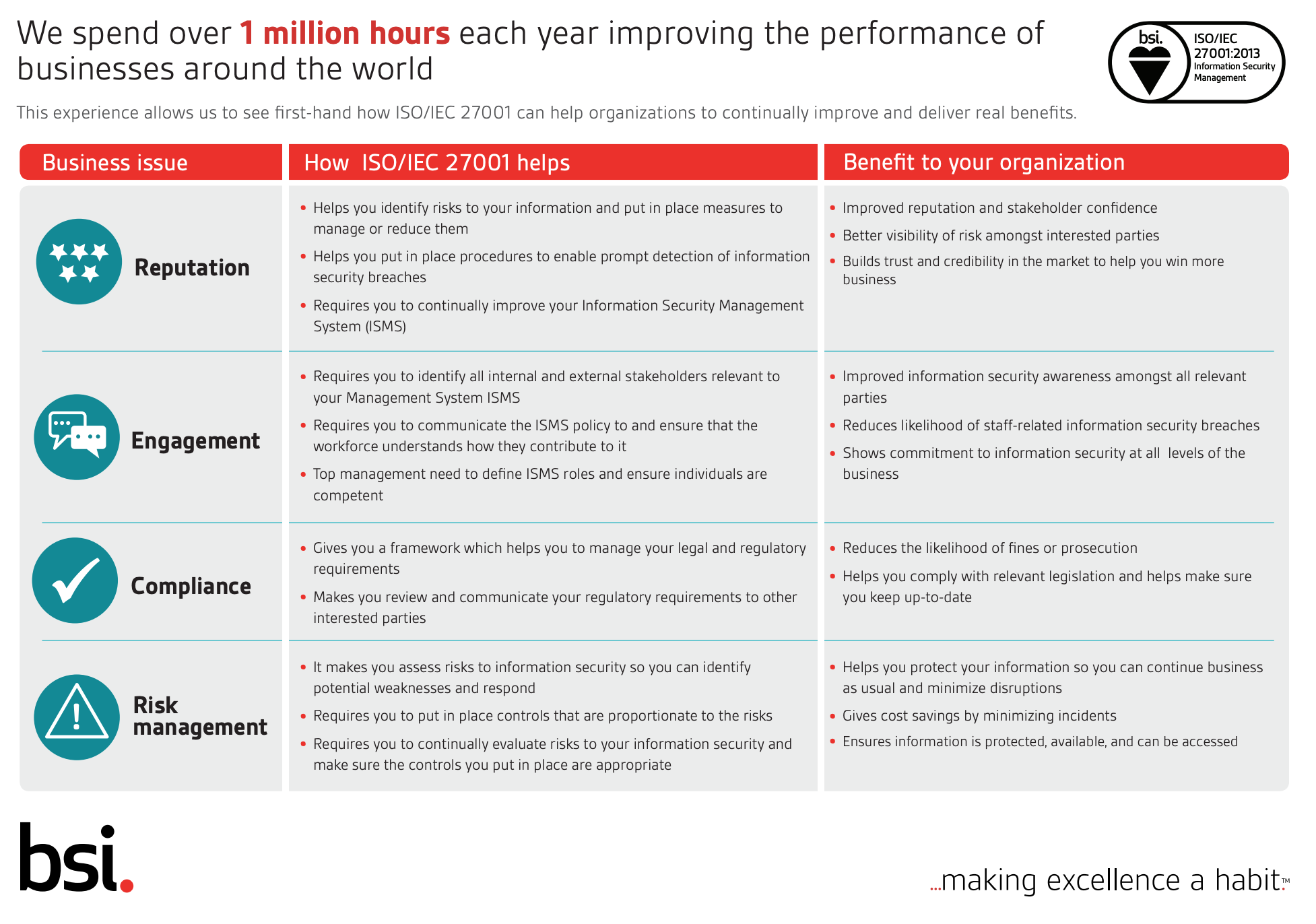
Critical across the event tech stack, in physical, virtual and hybrid events is the security of personal data. ISO27001 is the certification to check for here. As of last week, Glisser has passed this certification for a third straight year.
ISO27001 means that the data is not just technically secure, but the whole culture and work processes of a technology provider align with this approach. Some of the requirements include that no unprotected files containing data are flying around, no USB sticks with presentations left on desks, and a relatively simple compliance approval process for your use of the technology.
|
The image below courtesy of BSI, part of the UK National Standards body. |
 |
|
|








.png)
.png)
